Enterprise Solutions
We develop open, highly reliable and highly available solutions
Disig KeyPoint
Cloud solution for the qualified electronic signature or seal
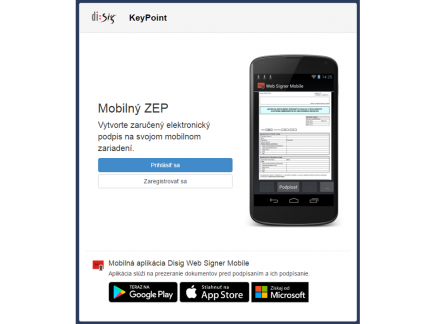
Creating QES without a smartcard
When creating an electronic signature, local storages of key material are usually used. These require the client to have a private key at their disposal. The private key is kept either in a software form (in a file) or on a QSCD device (on a smartcard).
A key material remote storage provided by the Disig KeyPoint system enables the end users to use the key material stored in a centrally administered secured device. This concept provides a similar level of security as common QSCD devices and also relieves the user from a necessity to own such a device and have the device physically attached to the system where the signing is carried out.
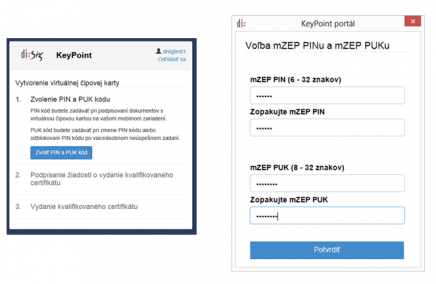
Mobile authentisation
The Disig KeyPoint system enables to link a physical identity with any device. This link may be subsequently used in case of two-phase authentification for any portal. Thus, the organisations that use the Disig KeyPoint do not need to maintain a database of authentication data.
Mobile eID
The key material stored in the Disig KeyPoint system is available for the clients regardless the platform and without a link to a specific device. Therefore, the user is able to create a signature using the same private key on a PC and on a mobile device (e.g. tablet or smartphone).
Basic characteristic
- the qualified electronic signature and seal may be created on any device
- multi-user systems working with the virtual smartcards concept
- safe storing and centralised management of cryptographic keys
- integration involving any multi-factor authentification system
- integration with a certification authority system for automatic certificates issuing
- practically unlimited number of users and keys
- trustworthy system certified by Slovak NSA for generation and storing of private keys and qualified certificates as well as for creation qualified electronic signatures or seals
Sole Control Level 2 as in CEN/TS 419241:2014
EU Regulation n. 910/2014 – eIDAS
CEN/TS 419241:2014 - Security Requirements for Trustworthy Systems Supporting Server Signing
Integration with the authentification system
Integration with the certification authority system
Integration with client´s system
THALES nShield F3 Solo with an active SEE functionality
THALES nShield F3 Connect an active SEE functionality
RSA with a key length up to 4096 bits
SHA-1
SHA-256, SHA-384, SHA-512
Microsoft Windows
Linux
Mac OS X
iOS
Windows Phone